We’re updating the Lightwire login flow to improve security and improve your experience while using the suite of Lightwire tools that can be found inside the partner portal, illume.
What's changing?
Logging into illume is now handled through the id.lightwire.co domain. Here’s what the login screen will look like in the new login flow (nothing ground breaking, I know). You can see the real changes once you’re logged in.

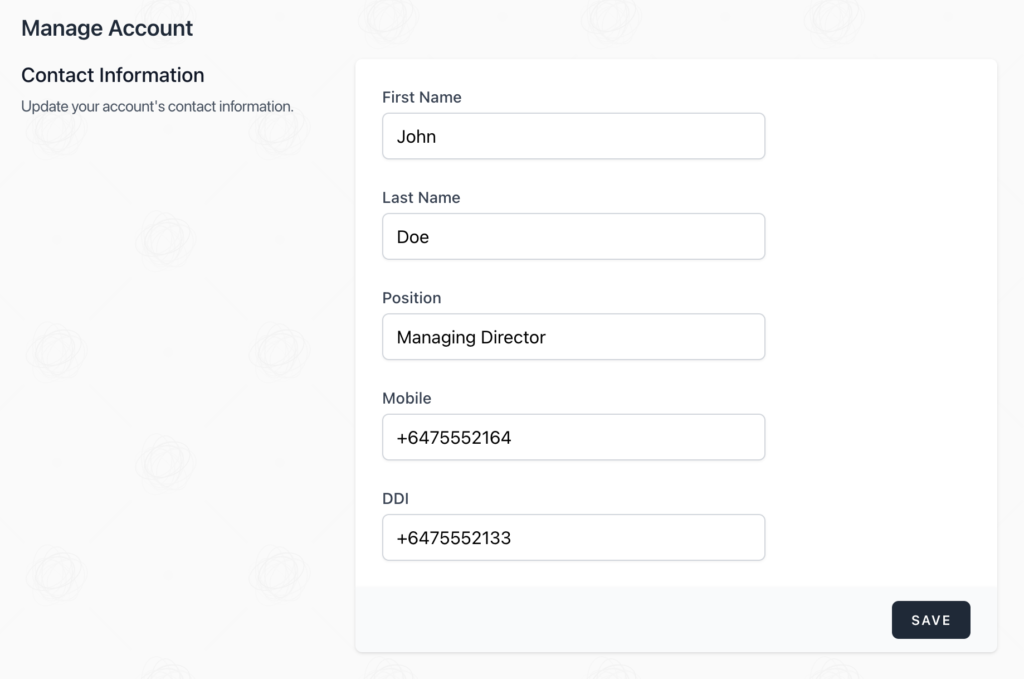
Once logged into illume, you can opt to change your contact details, password, manage browser sessions and/or log out other browser sessions, and set up two factor authentication.
Why are we implementing these changes?
The threat posed by cyber attacks is real. While we can’t completely prevent cyber attacks, we can mitigate the risk of one.
Passwords can be weak or reused across multiple accounts. They can also be stolen in a phishing or malware attack. The two factor authentication can prevent these incidents as an attacker would also need ‘something you have’ or ‘something you are’ to get access to the account.
Session management is another feature that enhances your security by allowing you to see details of current logged in sessions and enabling you to log out any other browser sessions.